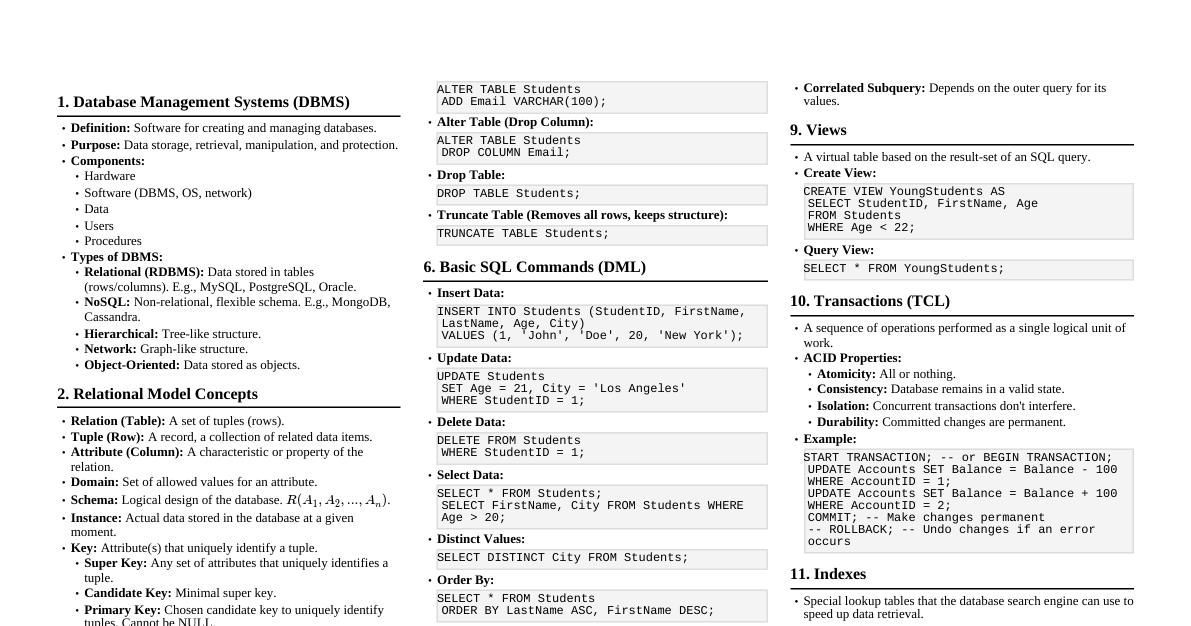
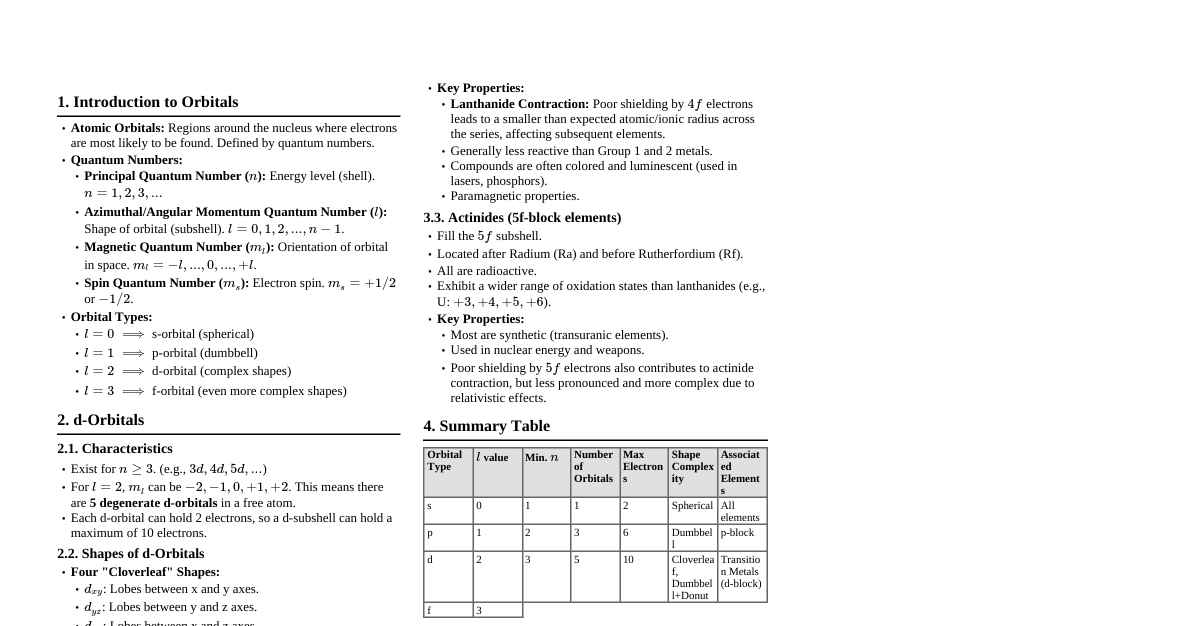
### Introduction to Asset Security Asset security is a critical component of information security, focusing on protecting an organization's valuable assets from unauthorized access, use, disclosure, disruption, modification, or destruction. Assets can be tangible (e.g., hardware, facilities) or intangible (e.g., data, intellectual property, reputation). The primary goal is to maintain the **confidentiality, integrity, and availability (CIA)** of these assets. #### Why Asset Security Matters - **Data Protection:** Safeguarding sensitive information from breaches. - **Business Continuity:** Ensuring operations can continue even after security incidents. - **Regulatory Compliance:** Meeting legal and industry standards (e.g., GDPR, HIPAA). - **Reputation Management:** Preventing damage to the organization's public image. - **Financial Stability:** Avoiding losses due to theft, fraud, or system downtime. ### Asset Identification & Classification The first step in securing assets is knowing what you have and how valuable it is. #### 1. Identification - **What are assets?** - **Information Assets:** Databases, files, intellectual property, contracts, customer data, financial records. - **Software Assets:** Operating systems, applications, utilities, custom code. - **Hardware Assets:** Servers, workstations, network devices, mobile devices, IoT devices. - **Physical Assets:** Facilities, data centers, storage media, documents. - **Services/People Assets:** Cloud services, third-party vendors, employees, contractors. - **Asset Inventory:** Create a comprehensive list of all assets. - **Tools:** Configuration Management Databases (CMDBs), asset management software, spreadsheets. - **Key Information:** Asset name, owner, location, type, value, dependencies. #### 2. Classification - **Purpose:** Assigning a level of sensitivity, value, and criticality to each asset. This dictates the security controls required. - **Classification Levels (Examples):** - **Public:** No harm if disclosed (e.g., marketing materials). - **Internal Use Only:** Restricted to internal personnel (e.g., internal memos). - **Confidential:** Disclosure could cause moderate harm (e.g., financial reports, HR data). - **Secret/Restricted:** Disclosure could cause severe harm (e.g., trade secrets, national security data). - **Criteria for Classification:** - **Confidentiality Impact:** What happens if this asset is disclosed? - **Integrity Impact:** What happens if this asset is modified or corrupted? - **Availability Impact:** What happens if this asset is unavailable? - **Legal/Regulatory Requirements:** Is this data subject to specific laws? - **Owner Responsibility:** Asset owners are typically responsible for classification. - **Review:** Classifications should be reviewed periodically. ### Asset Lifecycle Management Security controls must be applied throughout an asset's entire life. #### 1. Acquisition/Creation - **Secure by Design:** Integrate security requirements from the start. - **Vendor Assessment:** Evaluate security posture of third-party suppliers. - **Secure Configuration:** Deploy assets with hardened configurations. #### 2. Use/Operation - **Access Control:** Implement least privilege and need-to-know principles. - **Authentication:** Verify user identity (e.g., passwords, MFA, biometrics). - **Authorization:** Grant specific permissions based on roles. - **Monitoring & Auditing:** Track access and changes to assets. - **Logs:** Collect and review system and application logs. - **Intrusion Detection/Prevention Systems (IDPS):** Detect and block malicious activity. - **Data Protection:** - **Encryption:** Encrypt data at rest (storage) and in transit (network). - **Data Loss Prevention (DLP):** Prevent sensitive data from leaving controlled environments. - **Backup & Recovery:** Regularly back up critical data and test recovery procedures. - **Vulnerability Management:** - **Scanning:** Regularly scan for known vulnerabilities. - **Patch Management:** Apply security patches and updates promptly. - **Penetration Testing:** Simulate attacks to identify weaknesses. #### 3. Storage - **Physical Security:** Protect physical assets from unauthorized access. - **Environmental Controls:** Temperature, humidity, fire suppression. - **Access Controls:** Biometrics, keycards, surveillance. - **Logical Security:** Secure digital storage mechanisms. - **Storage Area Networks (SANs), Network Attached Storage (NAS).** - **Cloud Storage:** Ensure proper configuration of cloud security controls. #### 4. Disposal/Destruction - **Secure Erasure:** Ensure data is irrecoverably removed from storage media. - **Degaussing:** Eliminates magnetic data. - **Shredding/Pulverization:** Physical destruction for hard drives, paper. - **Wiping:** Overwriting data multiple times. - **Certification of Destruction:** Obtain documentation for compliance. - **Hardware Disposal:** Dispose of physical equipment environmentally and securely. ### Data Handling & Protection Data is often the most critical asset. Protecting it requires specific strategies. #### 1. Data Classification (Revisited) - **Granular Control:** Apply security based on data's classification. - **Tagging:** Label data with its classification level for automated enforcement. #### 2. Data Encryption - **At Rest:** Encrypt data stored on disks, databases, and backup media. - **Full Disk Encryption (FDE):** Encrypts entire storage devices. - **Database Encryption:** Encrypts specific fields or entire databases. - **In Transit:** Encrypt data as it travels over networks. - **TLS/SSL:** For web traffic (HTTPS). - **VPNs:** For secure network connections. - **SSH:** For secure remote access. - **Key Management:** Securely generate, store, and manage encryption keys. #### 3. Data Loss Prevention (DLP) - **Purpose:** Prevent sensitive information from leaving the organization's control. - **Mechanisms:** - **Network DLP:** Monitors outbound network traffic for sensitive data. - **Endpoint DLP:** Monitors data on workstations and servers. - **Storage DLP:** Scans data at rest for sensitive information. - **Policies:** Define rules for what data is sensitive and how it can be handled. #### 4. Data Masking & Anonymization - **Purpose:** Protect sensitive data while still allowing its use for testing, development, or analytics. - **Masking:** Replaces sensitive data with realistic but fake data (e.g., replacing credit card numbers with dummy numbers). - **Anonymization:** Removes personally identifiable information (PII) from datasets. - **Tokenization:** Replaces sensitive data with a non-sensitive equivalent (token) that has no extrinsic meaning. #### 5. Data Backups & Recovery - **Importance:** Essential for business continuity and disaster recovery. - **Strategy:** Follow the 3-2-1 Rule: - **3 copies** of your data (original + 2 backups). - On **2 different media types**. - With **1 copy offsite**. - **Testing:** Regularly test backup integrity and recovery procedures. - **Retention Policies:** Define how long backups are kept. ### Access Control Principles Controlling who can access assets is fundamental. #### 1. Identification, Authentication, Authorization (AAA) - **Identification:** Claiming an identity (e.g., username). - **Authentication:** Proving that identity (e.g., password, MFA). - **Something you know:** Password, PIN. - **Something you have:** Smart card, token, phone. - **Something you are:** Biometrics (fingerprint, iris scan). - **Somewhere you are:** Location-based authentication. - **Something you do:** Keystroke dynamics. - **Authorization:** Granting specific permissions based on authenticated identity. #### 2. Access Control Models - **Discretionary Access Control (DAC):** Owner of the resource grants/revokes access. - **Mandatory Access Control (MAC):** System-enforced, based on security labels (e.g., classified data). - **Role-Based Access Control (RBAC):** Permissions tied to user roles (most common in enterprises). - **Attribute-Based Access Control (ABAC):** Permissions based on attributes of user, resource, and environment. #### 3. Principles of Secure Access - **Least Privilege:** Users should only have the minimum access rights necessary to perform their job functions. - **Need-to-Know:** Access is granted only when it is essential for an individual to perform their duties. - **Separation of Duties:** No single individual should be able to complete a critical task alone. - **Job Rotation:** Regularly rotating employees through different job roles. - **Mandatory Vacations:** Requiring employees to take time off to uncover potential fraud or misuse. #### 4. Account Management - **Strong Passwords/Passphrases:** Enforce complexity, length, and uniqueness. - **Multi-Factor Authentication (MFA):** Require multiple forms of authentication. - **Account Provisioning:** Securely create and manage user accounts. - **Account De-provisioning:** Promptly disable/delete accounts for terminated employees or contractors. - **Privileged Access Management (PAM):** Securely manage and monitor accounts with elevated privileges. ### Physical & Environmental Security Protecting the physical space where assets reside. #### 1. Site Selection & Design - **Location:** Avoid high-risk areas (e.g., flood plains, active fault lines). - **Building Design:** Consider security from the ground up (e.g., reinforced walls, minimal windows). #### 2. Physical Access Controls - **Perimeter Security:** Fences, gates, security guards, surveillance cameras. - **Building Entry:** Access cards, biometrics, mantraps, turnstiles. - **Internal Security:** Locked server rooms, cabinets, restricted areas. - **Visitor Management:** Registration, escorts, temporary badges. #### 3. Environmental Controls - **Temperature & Humidity:** Maintain optimal conditions for equipment. - **HVAC Systems:** Heating, Ventilation, and Air Conditioning. - **Fire Prevention & Suppression:** - **Detectors:** Smoke, heat. - **Suppression Systems:** Sprinklers (pre-action), inert gas (e.g., FM-200, Novec 1230). - **Fire Extinguishers:** Clearly marked and accessible. - **Water Detection:** Sensors for leaks or flooding. - **Power Supply:** - **Uninterruptible Power Supplies (UPS):** Short-term power backup. - **Generators:** Long-term power backup. - **Surge Protectors:** Protect against power spikes. #### 4. Equipment Security - **Asset Tagging:** Inventory and track all physical assets. - **Cable Management:** Secure and label network and power cables. - **Locking Devices:** Physically secure equipment (e.g., server racks, laptops). - **Intrusion Detection:** Sensors on doors, windows, and critical equipment. ### Incident Response & Recovery What to do when security is breached. #### 1. Incident Response Plan (IRP) - **Preparation:** Develop and document an IRP. - **Team:** Establish an incident response team (IRT) with defined roles and responsibilities. - **Tools:** Acquire necessary forensic tools, communication channels. - **Training:** Regularly train IRT members. - **Identification:** Detect security incidents. - **Monitoring:** SIEM (Security Information and Event Management) systems, logs, alerts. - **Reporting:** Clear channels for users to report suspicious activity. - **Containment:** Limit the damage and prevent further spread. - **Isolation:** Disconnect affected systems. - **Segmentation:** Isolate network segments. - **Backup Restoration:** Restore clean systems from backups. - **Eradication:** Remove the cause of the incident. - **Malware Removal:** Clean infected systems. - **Vulnerability Patching:** Fix exploited vulnerabilities. - **System Hardening:** Implement stronger security controls. - **Recovery:** Restore systems and operations to normal. - **Validation:** Test restored systems for functionality and security. - **Monitoring:** Closely monitor recovered systems. - **Post-Incident Activity:** - **Lessons Learned:** Analyze what went wrong and how to improve. - **Reporting:** Document the incident for legal, compliance, and internal purposes. #### 2. Disaster Recovery Plan (DRP) - **Purpose:** Recover IT infrastructure and systems after a major disaster. - **Scope:** Addresses large-scale disruptions (natural disasters, major cyberattacks). - **Key Components:** - **Recovery Time Objective (RTO):** Maximum tolerable downtime. - **Recovery Point Objective (RPO):** Maximum tolerable data loss. - **Backup Strategy:** How and where data is backed up. - **Recovery Sites:** - **Hot Site:** Fully equipped, ready to go. - **Warm Site:** Partially equipped, requires some setup. - **Cold Site:** Basic infrastructure, requires significant setup. - **Testing:** Regularly test the DRP to ensure its effectiveness. #### 3. Business Continuity Plan (BCP) - **Purpose:** Maintain essential business functions during and after a disruption. - **Scope:** Broader than DRP, includes non-IT aspects (e.g., personnel, facilities, supply chain). - **Key Components:** - **Business Impact Analysis (BIA):** Identifies critical business functions and their dependencies. - **Continuity Strategies:** How to maintain operations (e.g., remote work, alternate suppliers). - **Crisis Communication:** How to communicate with stakeholders. - **Integration:** BCP, DRP, and IRP should be integrated and aligned. ### Regulatory & Compliance Requirements Adhering to laws, regulations, and industry standards. #### 1. Common Regulations & Frameworks - **GDPR (General Data Protection Regulation):** EU law on data protection and privacy. - **HIPAA (Health Insurance Portability and Accountability Act):** US law protecting health information. - **PCI DSS (Payment Card Industry Data Security Standard):** Standard for organizations handling credit card data. - **SOX (Sarbanes-Oxley Act):** US law on corporate financial reporting. - **ISO 27001:** International standard for Information Security Management Systems (ISMS). - **NIST Cybersecurity Framework:** US framework for managing cybersecurity risk. #### 2. Compliance Implications for Asset Security - **Data Retention:** Regulations dictate how long certain data must be kept. - **Data Disposal:** Specific requirements for secure destruction of sensitive data. - **Access Control:** Strict rules on who can access regulated data. - **Encryption:** Often mandated for sensitive data at rest and in transit. - **Auditing & Logging:** Requirements for logging access and changes to regulated assets. - **Incident Reporting:** Mandatory reporting of data breaches to authorities and affected individuals. #### 3. Auditing & Assurance - **Internal Audits:** Regular reviews by internal teams to ensure compliance. - **External Audits:** Independent third-party assessments. - **Penetration Testing:** Proactive testing to identify security weaknesses before auditors do. - **Documentation:** Maintain comprehensive records of security policies, procedures, and controls. - **Continuous Monitoring:** Implement systems to continuously monitor compliance status.