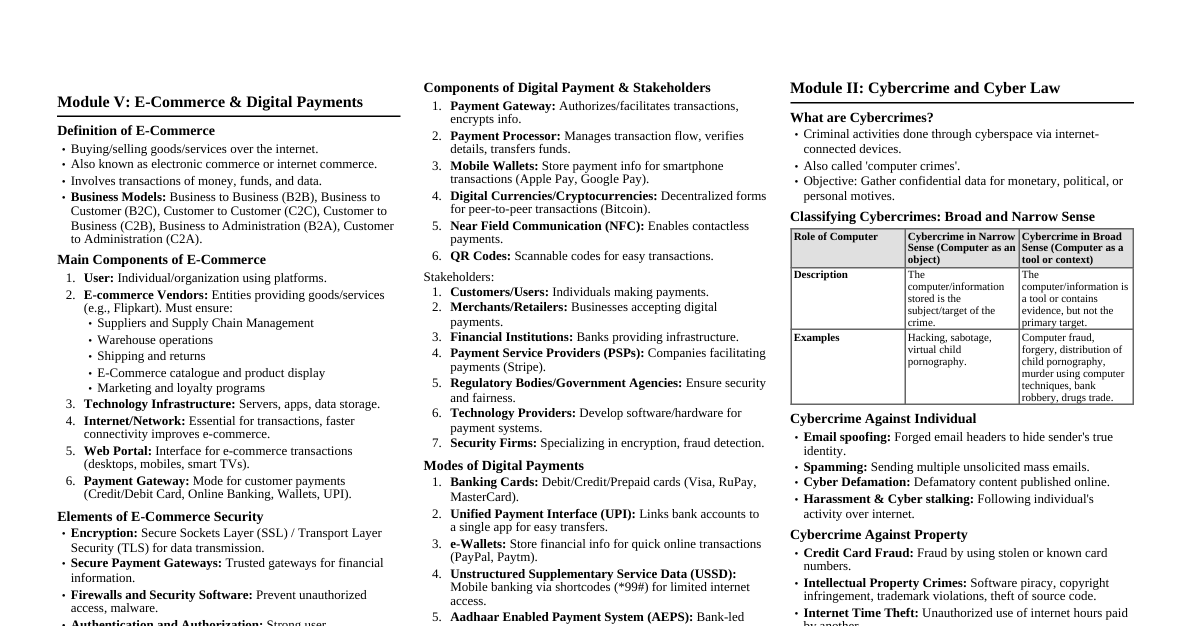
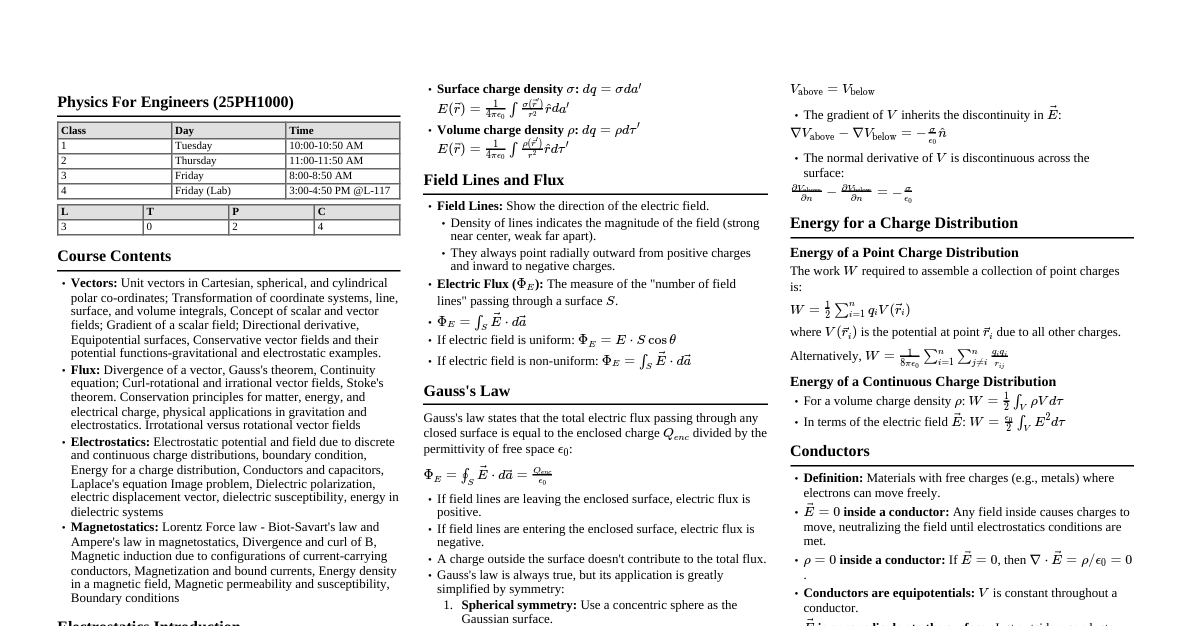
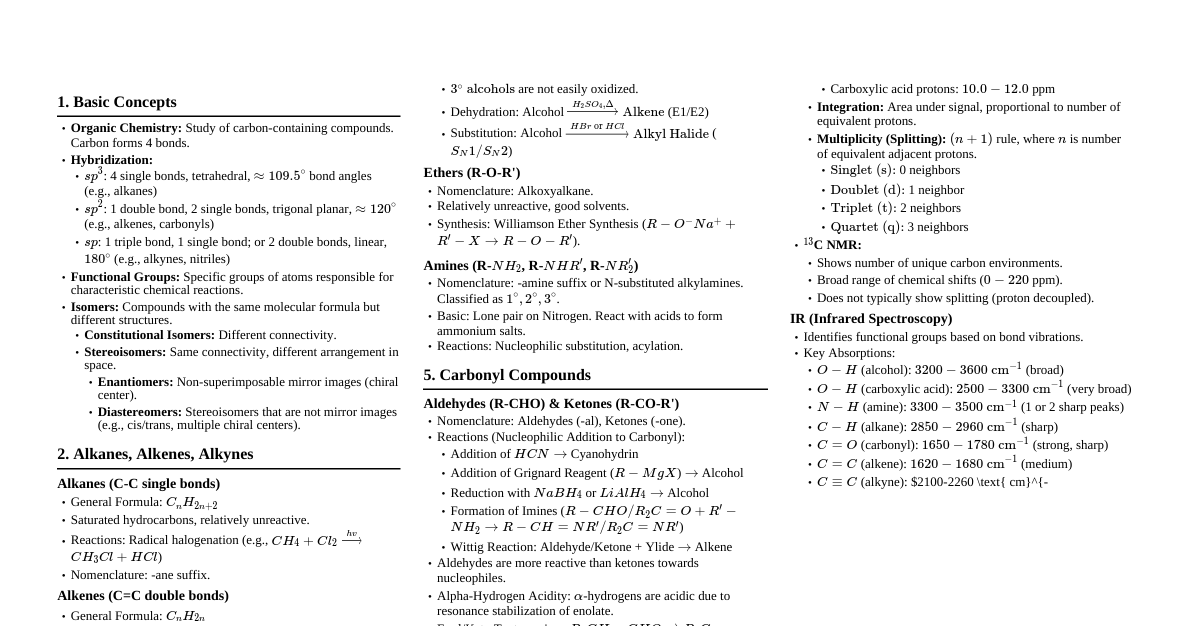
1. Core Concepts Confidentiality: Protecting information from unauthorized access. Achieved via encryption, access controls. Integrity: Ensuring information is accurate and untampered. Achieved via hashing, digital signatures. Availability: Ensuring authorized users can access information and systems when needed. Achieved via redundancy, backups, disaster recovery. Authentication: Verifying the identity of a user, process, or device. E.g., passwords, MFA. Authorization: Granting or denying specific permissions to an authenticated entity. E.g., ACLs. Non-repudiation: Proof of origin and integrity of data. E.g., digital signatures. 2. Common Attack Types Malware: Malicious software (viruses, worms, trojans, ransomware, spyware). Virus: Attaches to legitimate programs, requires user action to spread. Worm: Self-replicating, spreads across networks without user action. Trojan: Disguised as legitimate software, performs malicious actions. Ransomware: Encrypts data, demands payment for decryption. Phishing: Social engineering to trick users into revealing sensitive information or installing malware. Spear Phishing: Targeted phishing attacks. Whaling: Phishing targeting high-profile individuals. Denial of Service (DoS/DDoS): Overwhelming a system with traffic to make it unavailable. Man-in-the-Middle (MitM): Attacker intercepts communication between two parties. SQL Injection: Injecting malicious SQL code into input fields to manipulate databases. Cross-Site Scripting (XSS): Injecting malicious scripts into websites viewed by other users. Zero-Day Exploit: Exploiting a vulnerability before a patch is available. Brute Force: Systematically trying all possible combinations (e.g., passwords). 3. Cryptography Basics Encryption: Transforming data into an unreadable format. Symmetric Key: Same key for encryption and decryption. Fast but key distribution is a challenge. E.g., AES, DES. Asymmetric Key (Public Key): Different keys for encryption (public) and decryption (private). Slower but secure key exchange. E.g., RSA, ECC. Hashing: One-way function creating a fixed-size digest (hash) of data. Used for integrity checks. E.g., SHA-256, MD5 (deprecated). Digital Signature: Uses asymmetric cryptography to verify sender's identity and data integrity. Key Exchange: Methods to securely establish a shared secret key over an insecure channel. E.g., Diffie-Hellman. 4. Network Security Firewall: Monitors and controls incoming/outgoing network traffic based on predefined rules. Packet Filtering: Basic, checks headers (IP, port). Stateful Inspection: Tracks connections, more intelligent. Application Layer: Inspects traffic at the application level. IDS (Intrusion Detection System): Monitors network/system activities for malicious activity or policy violations. Passive. IPS (Intrusion Prevention System): Similar to IDS but can actively block detected threats. Active. VPN (Virtual Private Network): Creates a secure, encrypted tunnel over a public network. DMZ (Demilitarized Zone): A sub-network containing an organization's exposed public services. Network Segmentation: Dividing a network into smaller, isolated segments to control traffic and limit attack spread. 5. Security Best Practices Strong Passwords/Passphrases: Long, complex, unique. Multi-Factor Authentication (MFA): Requires two or more verification factors. E.g., something you know (password) + something you have (phone) + something you are (fingerprint). Regular Software Updates/Patching: Fixes known vulnerabilities. Principle of Least Privilege: Granting only the minimum necessary permissions for a user/process to perform its function. Data Backup & Recovery: Regular backups and a tested recovery plan. Security Awareness Training: Educating users about threats and safe practices. Incident Response Plan: Documented procedures for handling security incidents. Vulnerability Management: Discovering, prioritizing, and remediating vulnerabilities. Endpoint Security: Protecting individual devices (laptops, servers) from threats. 6. Security Models & Standards CIA Triad: Confidentiality, Integrity, Availability (fundamental security goals). Defense in Depth: Layered security approach to protect assets. Risk Management: Identify, assess, mitigate, monitor risks. $Risk = Threat \times Vulnerability \times Asset Value$ Compliance Frameworks: GDPR: General Data Protection Regulation (EU data privacy). HIPAA: Health Insurance Portability and Accountability Act (US healthcare data). PCI DSS: Payment Card Industry Data Security Standard (credit card data). ISO 27001: Information Security Management System standard. NIST Cybersecurity Framework: Identify, Protect, Detect, Respond, Recover. 7. Web Application Security OWASP Top 10 (2021): Broken Access Control Cryptographic Failures Injection Insecure Design Security Misconfiguration Vulnerable and Outdated Components Identification and Authentication Failures Software and Data Integrity Failures Security Logging and Monitoring Failures Server-Side Request Forgery (SSRF) Input Validation: Crucial for preventing injection attacks. Secure Coding Practices: Writing code that is resistant to common vulnerabilities. API Security: Protecting APIs from unauthorized access and misuse. 8. Incident Response Lifecycle Preparation: Establishing policies, teams, tools. Identification: Detecting and confirming a security incident. Containment: Limiting the scope and impact of the incident. Eradication: Removing the cause of the incident. Recovery: Restoring affected systems and data. Lessons Learned: Analyzing the incident to improve future responses.