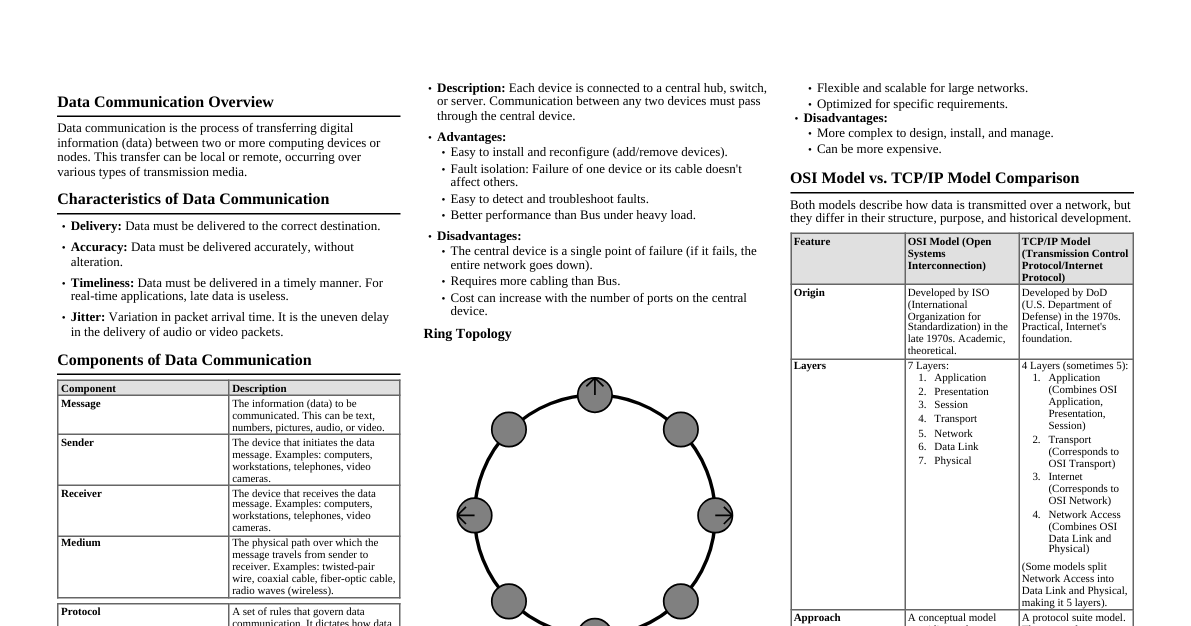
UNIT 1: Data Communication Networks Concepts 1.1 Data Transmission Modes These concepts describe fundamental characteristics of how data is sent and received across a network. Digital vs. Analog: Digital: Data represented by discrete, distinct values (typically 0s and 1s). Digital signals are robust to noise and can be easily processed and stored by computers. Think of a light switch: either on or off. Analog: Data represented by continuous, varying waveforms. Analog signals can carry more information but are more susceptible to noise and degradation over distance. Think of a dimmer switch: continuously variable light intensity. Parallel vs. Serial: Parallel: Multiple bits are transmitted simultaneously over multiple, separate communication lines (wires). This allows for very fast data transfer over short distances (e.g., within a computer bus or an older printer cable). However, it becomes costly and complex for longer distances due to issues like "skew" (bits arriving at different times). Serial: Bits are transmitted sequentially, one after another, over a single communication line. While inherently slower than parallel for a given clock speed, it's more cost-effective and reliable over long distances and at high speeds (e.g., USB, Ethernet, PCIe). Synchronous vs. Asynchronous: Synchronous: Data is transmitted in continuous blocks or frames, synchronized by a shared clock signal between the sender and receiver. This method is highly efficient as it minimizes overhead, making it suitable for high-speed, continuous data streams. Asynchronous: Data is transmitted character by character (or byte by byte), with each character framed by start and stop bits. This method is simpler to implement and suitable for irregular data flows (e.g., keyboard input) but has higher overhead due to the extra framing bits. Simplex, Half-Duplex, Full-Duplex: These terms describe the direction of data flow. Simplex: Data can flow in only one direction. The receiver cannot send data back to the sender. Example: Traditional radio or television broadcasting, where the audience only receives. Half-Duplex: Data can flow in both directions, but not simultaneously. Devices must take turns sending and receiving. Example: Walkie-talkies, where one person talks while the other listens. Full-Duplex: Data can flow in both directions simultaneously. This allows for continuous two-way communication. Example: A telephone conversation, where both parties can speak and listen at the same time. 1.2 Fundamental Concepts These are essential processes and techniques used in data communication. Encoding & Decoding: Encoding: The process of converting data (e.g., text, numbers) into a signal pattern (electrical voltage, light pulses) that can be transmitted over a communication medium. This involves mapping data bits to specific signal changes. Decoding: The reverse process, where the receiver converts the received signal pattern back into its original data form. Error Detection & Recovery: Mechanisms to ensure the integrity of data during transmission, as signals can be corrupted by noise or interference. Detection: Techniques like parity checks, checksums, and Cyclic Redundancy Checks (CRC) add redundant information to the data. The receiver uses this information to determine if errors occurred during transmission. Recovery (Correction): More advanced techniques, such as Forward Error Correction (FEC) codes or Automatic Repeat Request (ARQ), allow the receiver to either correct minor errors or request retransmission of corrupted data. Multiplexing: A technique that allows multiple data streams to share a single physical communication channel simultaneously, optimizing bandwidth usage. FDM (Frequency Division Multiplexing): Divides the total bandwidth of a medium into multiple, non-overlapping frequency bands. Each data stream is assigned a different frequency band. Example: Radio broadcasting, where different stations transmit on different frequencies. TDM (Time Division Multiplexing): Divides the access to a single channel into time slots. Each data stream is allocated a specific, recurring time slot to transmit its data. Example: Older digital telephone systems. WDM (Wavelength Division Multiplexing): A form of FDM used in fiber optic communication, where multiple data streams are transmitted simultaneously using different wavelengths (colors) of light over a single optical fiber. CDM (Code Division Multiplexing): Each data stream is given a unique "spreading code." All data streams transmit simultaneously over the same frequency band, but their unique codes allow the receiver to separate them. Example: CDMA cellular networks. Spreading (Spread Spectrum): A technique where a signal's bandwidth is intentionally spread over a much wider frequency band than the minimum required. This makes the signal more resistant to noise, interference, and jamming, and also allows for secure communication as it's harder to detect or intercept. CDMA is a type of spread spectrum technology. Modulation: The process of varying one or more properties (amplitude, frequency, or phase) of a periodic waveform (the carrier signal) with the information-carrying signal. This allows data to be transmitted efficiently over various media and facilitates multiplexing. AM (Amplitude Modulation): Varies the amplitude (strength) of the carrier wave according to the data signal. FM (Frequency Modulation): Varies the frequency of the carrier wave according to the data signal. PM (Phase Modulation): Varies the phase of the carrier wave according to the data signal. QAM (Quadrature Amplitude Modulation): Combines AM and PM to transmit more bits per symbol. 1.3 Network Topologies Network topology refers to the geometric arrangement of devices and communication channels in a network. It can be physical (how cables are laid out) or logical (how data flows). Bus Topology: All devices are connected to a single central cable, called the backbone or bus. Data transmitted by one device travels along the bus and is seen by all other devices. Only one device can transmit at a time. Simple and inexpensive for small networks, but a break in the backbone cable brings down the entire network. Bus Topology Star Topology: Each device in the network is connected to a central device (e.g., a hub, switch, or router) with its own dedicated cable. Data from one device goes to the central hub, which then forwards it to the destination. This is very common in modern LANs. It's robust because a failure in one cable only affects that device, but the central device is a single point of failure. Star Topology Ring Topology: Devices are connected in a closed loop, with each device connected directly to two other devices. Data travels in one direction around the ring. If one device fails, it can break the entire ring. Some ring networks (like FDDI) incorporate dual rings for redundancy. Token Ring is an example of a ring topology. Ring Topology Mesh Topology: Every device is connected directly to every other device. This provides high redundancy and fault tolerance, as there are many paths for data to travel. However, it's very expensive and complex to implement, especially for a large number of devices ($n(n-1)/2$ connections for $n$ devices). Often used for backbone networks or critical systems. Mesh Topology (Full) Tree Topology (Hierarchical): A combination of bus and star topologies. It has a root node, and all other nodes are connected to it in a hierarchical fashion, forming a tree-like structure. Often used in large networks to segment broadcasts and manage traffic. 1.4 Reference Models Reference models provide a conceptual framework for understanding how different network protocols and technologies interact. They help standardize network communication and allow different vendors' equipment to interoperate. OSI Model (Open Systems Interconnection) A 7-layer conceptual model developed by ISO to standardize communication functions. Each layer performs specific tasks and communicates with the layers directly above and below it. Data is encapsulated as it moves down the layers and decapsulated as it moves up. Physical Layer (Layer 1): Deals with the physical transmission of raw bit streams over the communication medium. It defines electrical, mechanical, procedural, and functional specifications for activating, maintaining, and deactivating physical links. Examples: Cables, connectors (RJ45), voltage levels, bit rates. Data Link Layer (Layer 2): Provides reliable data transfer across a physical link. It defines how data is formatted into "frames," handles physical addressing (MAC addresses), error detection and correction for the physical link, and flow control. Examples: Ethernet, PPP, MAC addresses. Network Layer (Layer 3): Responsible for logical addressing (IP addresses) and routing data packets across different networks. It determines the best path for data to travel from source to destination. Examples: IP (Internet Protocol), ICMP, routers. Transport Layer (Layer 4): Provides end-to-end communication between processes on different hosts. It ensures reliable and ordered delivery of data, handles segmentation/reassembly, flow control, and error recovery between applications. Examples: TCP (Transmission Control Protocol), UDP (User Datagram Protocol). Session Layer (Layer 5): Establishes, manages, and terminates communication sessions between applications. It provides dialogue control (who sends when) and synchronization (checkpointing data transfers). Examples: NetBIOS, RPC. Presentation Layer (Layer 6): Concerned with the syntax and semantics of the information transmitted. It handles data translation, encryption/decryption, and compression/decompression to ensure data is presented in a format that the application layer can understand. Examples: JPEG, MPEG, ASCII, SSL/TLS encryption. Application Layer (Layer 7): Provides network services directly to end-user applications. It allows users to interact with network resources. Examples: HTTP, FTP, SMTP, DNS, web browsers, email clients. 7. Application 6. Presentation 5. Session 4. Transport 3. Network 2. Data Link 1. Physical TCP/IP Model The TCP/IP model is a more practical and widely used protocol suite that forms the basis of the Internet. It's often described as a 4-layer or 5-layer model, mapping somewhat to the OSI model but with fewer layers and different responsibilities. Network Access Layer (or Link Layer): This layer combines the functionalities of the OSI Physical and Data Link layers. It defines how data is physically sent over the network medium and handles hardware addressing (MAC addresses). Examples: Ethernet, Wi-Fi. Internet Layer (or Network Layer): Corresponds directly to the OSI Network Layer. It's responsible for logical addressing (IP addresses) and routing packets across different networks (inter-networking). Examples: IP, ICMP, ARP. Transport Layer: Similar to the OSI Transport Layer, providing end-to-end communication between applications. It handles segmentation, reliability (TCP), and flow control. Examples: TCP, UDP. Application Layer: This layer combines the functions of the OSI Session, Presentation, and Application layers. It provides high-level protocols for specific applications and user services. Examples: HTTP, FTP, DNS, SMTP. Application (OSI L5-7) Transport (OSI L4) Internet (OSI L3) Network Access (OSI L1-2) UNIT 2: Communication Channels and Components 2.1 Wired Transmission Media These are physical cables that guide data signals from one point to another. Unshielded Twisted Pair (UTP): Consists of pairs of insulated copper wires twisted together. The twisting helps reduce electromagnetic interference (EMI) from external sources and crosstalk between adjacent pairs. Widely used in LANs (Ethernet). It's inexpensive and easy to install but susceptible to noise over longer distances. Shielded Twisted Pair (STP): Similar to UTP but includes an additional metallic foil or braid shield around the twisted pairs, or around individual pairs. This shielding provides better protection against EMI and crosstalk than UTP, making it suitable for environments with high electrical noise. It's more expensive and harder to install than UTP. Telephone Lines: Typically UTP cables, historically used for voice communication. With technologies like DSL (Digital Subscriber Line), they can also carry digital data over existing telephone networks, albeit with limited bandwidth compared to dedicated data cables. Coaxial Cables: Consists of a central copper conductor, an insulating layer, a metallic shield (braid or foil), and an outer insulating jacket. This construction provides excellent shielding against EMI. Used for cable TV, older Ethernet networks (10BASE2, 10BASE5), and some broadband internet connections. Baseband: Transmits digital signals directly without modulation onto a carrier frequency. It uses the entire cable capacity for a single channel. Example: Older Ethernet. Broadband: Transmits analog signals using modulation. It divides the cable's bandwidth into multiple frequency channels, allowing multiple signals (e.g., TV channels, internet) to be transmitted simultaneously. Example: Cable TV, modern cable internet. Optical Fiber Transmission: Transmits data as pulses of light through thin strands of glass or plastic fiber. It offers extremely high bandwidth, long transmission distances, and is immune to electromagnetic interference. It's widely used for high-speed backbone networks, long-haul communication, and increasingly in Fiber-to-the-Home (FTTH) deployments. Single-mode Fiber (SMF): Has a very small core diameter (8-10 microns), allowing only a single path for light to travel. This minimizes signal dispersion, enabling very long transmission distances and extremely high bandwidth. Used for long-haul and high-speed networks. Multi-mode Fiber (MMF): Has a larger core diameter (50-62.5 microns), allowing multiple paths (modes) for light to travel. This leads to more signal dispersion and limits transmission distance and bandwidth compared to SMF. Used for shorter distances, typically within buildings or campuses. 2.2 Wireless Transmission Media These media transmit data through electromagnetic waves without physical cables. Microwave Transmission: Uses high-frequency radio waves (typically 1-100 GHz) for line-of-sight communication. It requires clear paths between antennas and is susceptible to atmospheric conditions (rain fade). Used for long-distance terrestrial links, cellular backhaul, and satellite communication (ground stations). Infrared Transmission: Uses infrared light waves. It's short-range, requires a clear line of sight, and cannot penetrate opaque objects. Common applications include TV remote controls and short-range wireless communication between devices (e.g., IrDA ports on older laptops). Laser Transmission: Similar to infrared but uses highly coherent laser light. Offers very high bandwidth but is highly directional and extremely sensitive to atmospheric conditions (fog, rain, dust). Used for specialized high-speed point-to-point links where fiber is impractical. Radio Transmission: Uses radio frequency (RF) electromagnetic waves. It's versatile, can be omnidirectional or directional, and can penetrate walls depending on frequency. Covers a wide range of applications: Wi-Fi, Bluetooth, cellular networks, AM/FM radio, etc. Satellite Transmission: Involves sending signals to communication satellites orbiting Earth, which then retransmit them to other locations. Provides broad geographical coverage, including remote areas. However, it has significant latency (signal delay) due to the long distances involved. Geostationary Satellites (GEO): Orbit at ~36,000 km, appearing stationary from Earth. Provide wide coverage but high latency. Low Earth Orbit Satellites (LEO): Orbit at ~500-2000 km. Lower latency but require many satellites for continuous coverage (e.g., Starlink). VSAT (Very Small Aperture Terminal): Small, dish-shaped antennas used for two-way satellite communication, typically for data, internet, and voice services in remote locations or for backup links. 2.3 Network Connecting Devices Hardware components that facilitate communication and connectivity within and between networks. Hub: A basic Layer 1 (Physical Layer) device that connects multiple Ethernet devices in a star topology. When a hub receives data on one port, it simply broadcasts (repeats) that data to all other ports. This creates a single collision domain, leading to inefficient bandwidth usage and potential collisions in busy networks. Switch: A more intelligent Layer 2 (Data Link Layer) device that connects multiple Ethernet devices. Unlike a hub, a switch learns the MAC addresses of devices connected to its ports and forwards frames only to the intended destination port. This creates separate collision domains for each port, significantly improving network performance and security. Router: A Layer 3 (Network Layer) device that connects different networks (e.g., a LAN to the Internet). Routers use IP addresses to determine the best path for data packets to travel between networks. They maintain routing tables and are responsible for forwarding packets across different broadcast domains. Bridge: A Layer 2 device that connects two LAN segments (e.g., two Ethernet segments) and filters traffic based on MAC addresses. It helps reduce traffic on each segment by forwarding only frames destined for devices on the other segment. Switches are essentially multi-port bridges. Repeater: A Layer 1 device that regenerates and retransmits signals to extend the maximum distance of a network segment. It essentially boosts the signal strength to overcome attenuation, but it does not filter or interpret data. Gateway: A network device (can be a router, firewall, server, or other specialized device) that acts as an entry or exit point for a network. It often translates protocols between different networks, allowing them to communicate. Gateways can operate at any layer of the OSI model, but are often associated with Application Layer protocol translation. 2.4 Switching Techniques Methods used to move data through a network from source to destination. Circuit Switching: A dedicated communication path (circuit) is established between the sender and receiver before any data transmission begins. This circuit remains exclusively allocated for the duration of the communication, even if no data is being sent. Once the communication ends, the circuit is released. Example: Traditional public switched telephone network (PSTN). Pros: Guaranteed bandwidth, constant transmission delay, suitable for real-time applications like voice calls. Cons: Inefficient use of network resources (circuit idle during silent periods), setup delay before communication can begin, network resources are reserved even if not fully utilized. Packet Switching: Data is broken down into smaller, fixed-size or variable-size units called "packets." Each packet is then transmitted independently through the network, potentially taking different paths, and reassembled at the destination. No dedicated circuit is established. Example: The Internet. Pros: Efficient use of network resources (shared paths), robust to failures (packets can reroute), no call setup delay, bursty data traffic handled well. Cons: Variable delay (latency and jitter) due to congestion and routing decisions, requires more complex protocols for error control and reassembly, potential for out-of-order packet arrival. Message Switching: The entire message is treated as a single unit and stored at intermediate nodes ("store-and-forward") before being forwarded to the next node. Each message contains the full destination address. This technique is largely obsolete for real-time data but is conceptually similar to how email used to be handled in early networks. UNIT 3: Data Link Layer The Data Link Layer (Layer 2) is responsible for reliable transfer of data frames across a physical link. It handles physical addressing, error detection, and flow control to ensure data integrity over a single network segment. 3.1 Design Issues Key challenges and functionalities addressed by the Data Link Layer. Services Provided to the Network Layer: The Data Link Layer offers various services to the Network Layer above it, depending on the application's reliability needs: Unacknowledged Connectionless Service: Sends frames without connection setup or acknowledgment. Fast but unreliable. Suitable for real-time audio/video or low-error links. Acknowledged Connectionless Service: Sends frames without connection setup but requires acknowledgments. Retransmits lost frames. More reliable than unacknowledged. Acknowledged Connection-Oriented Service: Establishes a logical connection, sends frames, acknowledges receipt, and handles retransmissions. Most reliable service, guaranteeing ordered delivery. Framing: The process of dividing the continuous stream of bits from the Physical Layer into discrete blocks of data called "frames." Frames are essential for error detection, flow control, and addressing at the Data Link Layer. Character Count: A field in the frame header specifies the number of characters (bytes) in the frame. If this count is corrupted, the receiver cannot accurately determine the frame boundaries. Byte Stuffing (Character Stuffing): Uses special flag bytes (e.g., 01111110 ) to mark the beginning and end of a frame. If the flag byte pattern appears in the data, a special "escape" byte is inserted (stuffed) before it to distinguish it from a true flag. The receiver unstuffs these bytes. Bit Stuffing: Similar to byte stuffing but operates at the bit level. A flag bit pattern (e.g., 01111110 ) marks frame boundaries. If five consecutive '1' bits appear in the data, a '0' bit is automatically inserted (stuffed) by the sender. The receiver removes (unstuffs) this extra '0'. Physical Layer Coding Violations: Some physical layer encoding schemes have "illegal" bit patterns (e.g., in Manchester encoding, a transition always occurs in the middle of a bit period). These illegal patterns can be used to mark frame boundaries, as they cannot occur within the data itself. Error Control: Mechanisms to detect and correct errors that occur during transmission over the physical link. This ensures that frames are delivered intact and in the correct order to the Network Layer. Error Detection Codes: (e.g., Parity, Checksum, CRC) detect if a frame has been corrupted. Automatic Repeat Request (ARQ): Protocols that combine error detection with retransmission requests. If an error is detected, the receiver requests the sender to retransmit the corrupted frame. Common ARQ variants include Stop-and-Wait, Go-Back-N, and Selective Repeat. Flow Control: Mechanisms to prevent a fast sender from overwhelming a slower receiver with too much data. This ensures that the receiver has enough buffer space and processing capability to handle incoming frames. Stop-and-Wait: The sender transmits one frame and then waits for an acknowledgment (ACK) from the receiver before sending the next frame. Simple but inefficient for long delays. Sliding Window: Allows the sender to transmit multiple frames (a "window" of frames) before waiting for acknowledgments. The window size determines the number of unacknowledged frames that can be in transit. This improves efficiency, especially over links with high latency. 3.2 Data Link Layer Protocols Specific protocols implementing Data Link Layer functionalities. HDLC (High-Level Data Link Control): A bit-oriented, synchronous data link protocol widely used for point-to-point and multipoint communication. It defines frame formats, error control (CRC), and flow control (sliding window). HDLC forms the basis for many other data link protocols. SDLC (Synchronous Data Link Control): Developed by IBM, it's an earlier version of a bit-oriented protocol that influenced HDLC. It was primarily used in IBM's SNA (Systems Network Architecture). Data Link Layer in the Internet: For connecting to the Internet, particularly over serial lines (dial-up, DSL, fiber to home), specific data link protocols are used. SLIP (Serial Line Internet Protocol): An older, simple protocol for encapsulating IP datagrams over serial lines. It lacks error checking, authentication, and dynamic addressing, making it largely obsolete. PPP (Point-to-Point Protocol): The standard protocol for connecting computers over serial lines (e.g., dial-up, DSL, PPPoE for fiber). PPP provides robust features including: Framing for IP datagrams. Link Control Protocol (LCP) for establishing, configuring, and testing the data link. Network Control Protocols (NCPs) for configuring different network layer protocols (e.g., IPCP for IP). Authentication (PAP, CHAP). Error detection. 3.3 MAC Sub-layer (Medium Access Control) The MAC sub-layer is a sub-layer of the Data Link Layer, specifically addressing how multiple devices share a common physical transmission medium (e.g., an Ethernet cable, radio spectrum) without interfering with each other. It governs access to the shared channel. ALOHA: A very early and simple random access protocol. When a station has data to send, it just sends it. If a collision occurs (two or more stations transmit simultaneously), the stations detect the collision, wait a random amount of time, and retransmit. Pure ALOHA: No sensing of the channel. Stations transmit whenever they have data. Very inefficient (max throughput ~18%). Slotted ALOHA: Time is divided into discrete slots. Stations can only begin transmission at the start of a slot. This slightly improves efficiency (max throughput ~36%). CSMA/CD (Carrier Sense Multiple Access with Collision Detection): A protocol used in traditional wired Ethernet. Stations "sense" the carrier (listen to the medium) before transmitting. If the medium is idle, they transmit. If the medium is busy, they wait. While transmitting, they continue to monitor the medium for collisions. If a collision is detected, all transmitting stations immediately stop, send a jamming signal, wait a random backoff time, and then attempt to retransmit. This reduces collisions but doesn't eliminate them. CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance): A protocol used in wireless networks (Wi-Fi) where collision detection is difficult or impossible (e.g., due to hidden node problem). Stations sense the carrier. If busy, they wait. If idle, they wait a short interframe space (IFS), then transmit. To further avoid collisions, it often uses Request to Send (RTS)/Clear to Send (CTS) handshaking and explicit acknowledgments (ACKs) for successful reception. If an ACK is not received, retransmission is assumed. IEEE Standards: The Institute of Electrical and Electronics Engineers (IEEE) develops standards for local and metropolitan area networks. 802.3: Defines Ethernet, including physical layer and MAC sub-layer specifications (e.g., CSMA/CD). 802.11: Defines Wireless LAN (WLAN) technologies, commonly known as Wi-Fi. Specifies MAC (e.g., CSMA/CA) and physical layer aspects for wireless communication. 802.15: Defines Wireless Personal Area Networks (WPANs), including Bluetooth. 802.16: Defines Wireless Metropolitan Area Networks (WMANs), known as WiMAX. Multiple Access Techniques (for shared wireless media): FDMA (Frequency Division Multiple Access): Divides the available frequency spectrum into multiple, non-overlapping frequency bands. Each user or channel is assigned a unique frequency band for the duration of their communication. Example: Analog cellular systems, traditional radio broadcasting. TDMA (Time Division Multiple Access): Divides the available time into discrete time slots. Each user is assigned a specific, recurring time slot to transmit their data on the same frequency. Example: GSM cellular systems. CDMA (Code Division Multiple Access): Allows multiple users to transmit simultaneously over the same frequency band. Each user's data is spread using a unique "spreading code." Receivers use the same code to extract the intended signal while rejecting others. Example: CDMA cellular systems (e.g., Verizon, Sprint in the past). 3.4 WAN Technologies Technologies primarily used for Wide Area Networks (WANs) to connect geographically dispersed LANs. Frame Relay: A packet-switching technology designed for efficient data transmission over WANs. It's a connection-oriented service (logical circuits) but simpler and faster than older X.25 because it assumes reliable lines and performs error correction only at the endpoints, not at every intermediate node. This "fast packet" approach reduces overhead and latency. ATM (Asynchronous Transfer Mode): A high-speed, connection-oriented switching technology that transmits all data in small, fixed-size cells (53 bytes). Designed to handle voice, video, and data traffic with guaranteed Quality of Service (QoS). ATM was envisioned as a universal networking technology but has largely been superseded by IP/Ethernet for most applications, though it still exists in some backbones (e.g., DSL access networks). UNIT 4: LAN and WAN Network 4.1 LAN Technologies Technologies used to build Local Area Networks (LANs) within a limited geographical area. Ethernet (IEEE 802.3): The most dominant LAN technology. Originally used CSMA/CD on shared coaxial cables, but modern Ethernet primarily uses switches in a star topology with dedicated full-duplex links. It supports various speeds (e.g., Fast Ethernet 100 Mbps, Gigabit Ethernet 1 Gbps, 10 Gigabit Ethernet, etc.) over twisted-pair copper or fiber optic cables. Token Ring (IEEE 802.5): A LAN technology where devices are connected in a physical ring or star-wired ring topology. Access to the network is controlled by a "token" that circulates around the ring. Only the station holding the token can transmit. This provides deterministic access but is less flexible and has largely been replaced by Ethernet. FDDI (Fiber Distributed Data Interface): A high-speed token-passing network standard (100 Mbps) that uses fiber optic cables. It typically uses a dual-ring topology for redundancy and fault tolerance, making it suitable for backbone networks in large organizations. Like Token Ring, it has largely been replaced by Gigabit Ethernet. Wireless LANs (WLANs - IEEE 802.11): Commonly known as Wi-Fi. It uses radio waves to connect devices without physical cables, providing mobility. WLANs operate under the IEEE 802.11 family of standards (e.g., 802.11a/b/g/n/ac/ax) and typically use CSMA/CA for medium access control. An Access Point (AP) acts as a central hub for wireless clients. Virtual LANs (VLANs): A logical grouping of network devices that allows them to communicate as if they were on the same physical LAN, even if they are connected to different physical switch ports or even different switches. VLANs segment broadcast domains, improve security, and enhance network management by separating traffic (e.g., voice, data, guest access) without requiring separate physical infrastructure. 4.2 WAN: Network Layer (Addressing and Routing) The Network Layer is crucial for WAN communication, enabling data to travel across multiple interconnected networks (internetworks). Addressing: Unique identifiers for devices that allow them to be located and addressed across different networks. IP Addresses: Logical addresses used at the Network Layer to uniquely identify a device on an IP network. IPv4: A 32-bit address (e.g., 192.168.1.1), typically written in dotted-decimal notation. It has a limited address space, which is largely exhausted. IPv6: A 128-bit address (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334), typically written in hexadecimal. Designed to provide a vast address space and improved features. Subnetting/CIDR (Classless Inter-Domain Routing): Techniques to divide a large IP network address space into smaller, more manageable subnetworks. This improves efficiency, security, and reduces broadcast traffic. CIDR allows for flexible allocation of IP address blocks. Routing: The process of selecting the best path for data packets to travel from a source host on one network to a destination host on another network. Routers perform this function by consulting their routing tables. Routing Methods: Static Routing: Routes are manually configured by a network administrator. They are fixed and do not change unless manually updated. Suitable for small, stable networks or for specific purposes (e.g., default routes). Pros: Simple to configure, secure (no routing updates exchanged), low overhead. Cons: Not scalable, requires manual intervention for changes or failures, cannot adapt to network topology changes. Dynamic Routing: Routers automatically discover and learn network routes by exchanging routing information with other routers using routing protocols. They can adapt to changes in network topology (e.g., link failures, new routes). Pros: Scalable, adapts to network changes, reduces administrative overhead. Cons: More complex to configure, consumes network bandwidth for routing updates, more processing power required on routers. 4.3 Dynamic Routing Protocols Protocols that enable routers to dynamically share and update routing information. Distance Vector Protocol: Routers exchange their entire routing tables with their directly connected neighbors. Each router computes the "distance" (cost) to destinations and the "vector" (next hop) to reach them. They rely on neighbors' information to build their own tables. Example: RIP (Routing Information Protocol). Problem: "Counting to infinity" problem, where incorrect route information can propagate slowly, leading to routing loops and slow convergence after network changes. Techniques like split horizon and poison reverse are used to mitigate this. Link State Protocol: Routers exchange only information about their directly connected links (Link State Advertisements - LSAs) with all other routers in the same routing area. Each router then uses this collected link-state information to construct a complete topological map of the network. From this map, each router independently calculates the shortest path to all destinations using an algorithm like Dijkstra's. Example: OSPF (Open Shortest Path First). Pros: Fast convergence, less prone to routing loops, provides a complete view of the network topology. Cons: More complex to configure and manage, requires more processing power and memory on routers. Open Shortest Path First (OSPF): A widely used interior gateway protocol (IGP) for large enterprise networks. It's a link-state routing protocol that uses Dijkstra's algorithm to calculate the shortest path. OSPF supports hierarchical routing using "areas" to improve scalability and reduce routing traffic. BGP (Border Gateway Protocol): The primary exterior gateway protocol (EGP) used for routing between different autonomous systems (AS) on the Internet. BGP is a path-vector protocol, exchanging reachability information and path attributes rather than just distances. It's highly complex and allows network administrators to implement routing policies. 4.4 Internet Protocol Suite Core protocols that define how the Internet works. Internet Protocol (IP): The fundamental protocol of the Internet Layer. It's a connectionless, unreliable protocol responsible for addressing and routing data packets (datagrams) from a source host to a destination host across multiple networks. IP itself does not guarantee delivery, order, or error-free transmission; these are handled by higher-layer protocols (e.g., TCP). Addressing & Routing: IP defines the logical addressing scheme (IPv4 and IPv6) and the mechanisms by which routers forward packets based on these addresses. Internet Control Message Protocol (ICMP): A supporting protocol for IP, used primarily for sending error messages and operational information indicating, for example, that a requested service is not available or that a host or router could not be reached. Examples: The ping command uses ICMP Echo Request/Reply, and traceroute uses ICMP for path discovery. Address Resolution Protocol (ARP): Used to map an IP address (Network Layer) to a physical MAC address (Data Link Layer) within a local network segment. When a device wants to send an IP packet to another device on the same LAN, it uses ARP to find the destination's MAC address corresponding to its IP address. Dynamic Host Configuration Protocol (DHCP): A network protocol used to dynamically assign IP addresses and other network configuration parameters (e.g., subnet mask, default gateway, DNS servers) to devices connected to a network. This automates network setup and prevents IP address conflicts. 4.5 Transport Layer Protocols (Process-to-Process Delivery) These protocols provide communication services directly to application processes running on hosts. They handle logical communication between application programs. UDP (User Datagram Protocol): A connectionless, unreliable transport protocol. It provides minimal services, simply taking data from the application, adding port numbers for process-to-process delivery, and passing it to the IP layer. UDP offers no guarantees of delivery, order, or error checking. It's fast and has low overhead, making it suitable for applications where speed is critical and some data loss is acceptable. Examples: DNS queries, streaming audio/video, online gaming. TCP (Transmission Control Protocol): A connection-oriented, reliable transport protocol. It establishes a logical connection between two application processes, ensures data is delivered reliably, in order, and without errors. TCP handles segmentation, reassembly, flow control, and congestion control. It's the backbone for many critical Internet applications. Examples: HTTP, FTP, Email (SMTP). Three-way Handshake: A three-step process used by TCP to establish a reliable connection between a client and a server before data transfer begins. Client sends SYN (synchronize sequence number). Server responds with SYN-ACK (synchronize-acknowledge). Client responds with ACK (acknowledge). Congestion Control: Mechanisms within TCP to prevent the network from becoming overloaded (congested). TCP dynamically adjusts the sending rate based on network conditions (e.g., packet loss, round-trip time) to avoid causing or exacerbating congestion. Slow Start: Increases the sending rate exponentially at the beginning of a connection or after congestion. Congestion Avoidance: Increases the sending rate linearly to probe for available bandwidth. Fast Retransmit/Recovery: Mechanisms to quickly retransmit lost segments without waiting for a retransmission timeout, improving performance during moderate packet loss. SCTP (Stream Control Transmission Protocol): A newer transport layer protocol that combines features of both TCP and UDP. It's message-oriented (like UDP) but reliable and connection-oriented (like TCP). Key features include: Multi-streaming: Allows multiple independent data streams within a single SCTP association, preventing head-of-line blocking. Multi-homing: Allows a single SCTP endpoint to have multiple IP addresses, providing redundancy and fault tolerance. Reliable, ordered delivery of data within each stream. Primarily used in telephony signaling (e.g., SS7 over IP) and some mission-critical applications. UNIT 5: Application Layer Protocols The Application Layer (Layer 7 in OSI, top layer in TCP/IP) provides direct services to end-user applications. These protocols define how applications exchange data over the network. 5.1 Client/Server Model A fundamental distributed computing model where "clients" (e.g., web browsers, email clients) request services or resources from "servers" (e.g., web servers, email servers). The server listens for requests, processes them, and sends back responses. This model is ubiquitous on the Internet. Client Server Request Response 5.2 Common Application Protocols These protocols define the format and rules for data exchange between applications. NFS (Network File System): A distributed file system protocol that allows users to access files and directories located on remote computers over a network as if they were local. This enables centralized file storage and sharing. Telnet (Telecommunication Network): An older network protocol used to provide a command-line interface for remote login to servers. It transmits data in plain text, making it highly insecure as credentials and data can be easily intercepted. Largely replaced by SSH (Secure Shell). FTP (File Transfer Protocol): A standard network protocol used for transferring files between a client and a server on a computer network. FTP uses two separate connections: a control connection (for commands and responses) and a data connection (for actual file transfer). Like Telnet, it often transmits data unencrypted. E-mail System: A suite of protocols for sending, receiving, and managing electronic mail. SMTP (Simple Mail Transfer Protocol): Used for sending emails from an email client to an email server, and for transferring emails between mail servers. It acts as the "push" mechanism for email. POP (Post Office Protocol, primarily POP3): Used by email clients to retrieve emails from a mail server. POP3 typically downloads emails to the local device and then deletes them from the server, making it less suitable for accessing email from multiple devices. IMAP (Internet Message Access Protocol, primarily IMAP4): Also used by email clients to retrieve emails. IMAP allows users to manage emails directly on the mail server, synchronize email status (read/unread, deleted) across multiple devices, and access only message headers if desired, saving bandwidth. WWW (World Wide Web): A global system of interconnected computer networks that uses HTTP to transmit data. It's an information system where documents and other web resources are identified by URLs, interconnected by hyperlinks, and accessible via the Internet. DNS (Domain Name System): A hierarchical and decentralized naming system for computers, services, or any resource connected to the Internet or a private network. Its primary function is to translate human-readable domain names (e.g., www.example.com ) into numerical IP addresses (e.g., 192.0.2.1 ) that computers use to identify each other. HTTP (Hypertext Transfer Protocol): The foundation protocol for data communication on the World Wide Web. It's a client-server protocol used for retrieving resources (like HTML pages, images, videos) from web servers. HTTP is stateless, meaning each request from a client to a server is treated as an independent transaction. HTTPS (Hypertext Transfer Protocol Secure): The secure version of HTTP. It encrypts communication between a web browser and a web server using SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols, providing data confidentiality and integrity. HTML (Hypertext Markup Language): The standard markup language for creating web pages and web applications. It uses a system of "tags" to structure content (headings, paragraphs, lists), embed media (images, videos), and create hyperlinks, defining the content and structure of web documents.