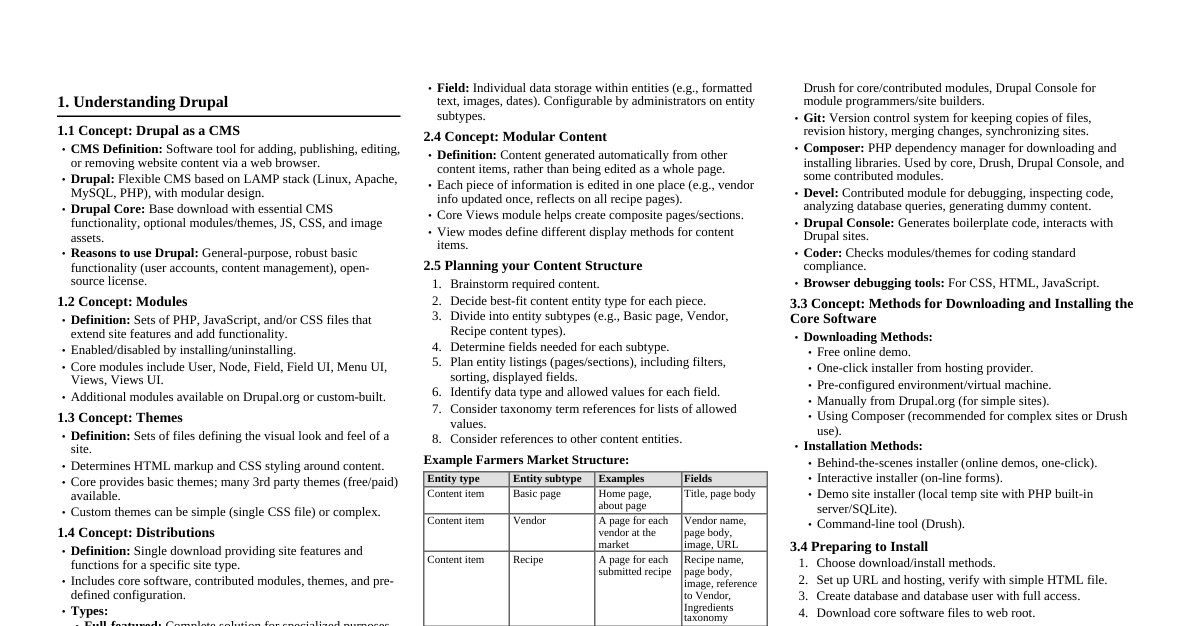
CDPSE Certification Overview Purpose: Comprehensive study guide for the CDPSE certification, established by ISACA in 2020. Audience: Aspiring and practicing privacy professionals, IT, security, and business management. Key Domains: Privacy Governance, Privacy Architecture, Data Cycle. Earning & Maintaining CDPSE Requirements: Pass the CDPSE exam. Submit verifiable evidence of 5 years experience (3 in CDPSE job practice areas). Adhere to ISACA’s Code of Professional Ethics. Complete 20 CPEs annually (120 over 3 years). Pay annual maintenance fees. Experience Areas: Privacy Governance (34% of exam) Privacy Architecture (36% of exam) Data Cycle (30% of exam) Substitutions: CISA, CISM, CGEIT, CRISC, CSX-P, FIP certifications can substitute up to 2 years. Exam Details: Computerized, multiple-choice (100+ questions), 4 choices/question, 1 best answer. ISACA Code of Professional Ethics (Paraphrased) Promote effective management of information systems. Act with objectivity, due diligence, and professional care. Perform duties legally, upholding professional conduct. Ensure privacy and confidentiality; do not use sensitive info for personal gain. Commit to continuous learning and encourage others. Ensure truth and accuracy in reporting; do not mislead. Exam Preparation Tips Refer to ISACA website for latest info. Register and schedule early. Familiarize with job practice areas. Know your learning style. Use practice exams for self-assessment. Study iteratively (2-6 months recommended). Avoid cramming. Consider study groups. Check logistics (confirmation letter, test center location). Pack essentials (ID, confirmation). Get adequate sleep. Dress comfortably, arrive early. Observe test rules. Answer all questions (mark and return if unsure). Privacy Governance (34% of Exam) Introduction to Privacy Governance Definition: Senior management's strategic control over business functions through policies, objectives, delegation, and monitoring. Purpose: Ensure privacy strategy aligns with laws, organizational goals, and evolving regulations. Components: Privacy policy, data governance, compliance, risk management, cybersecurity. Privacy is a business issue: Requires understanding and commitment from all levels, from board to individual contributor. Legal Counsel: Essential for ensuring policies and practices comply with laws like GDPR, CCPA. Privacy & Security: Interdependent; privacy cannot succeed without effective cybersecurity. Privacy Governance Influencers Nature of Personal Data: Information about people (customers, employees, etc.) is often sensitive; requires safeguarding and proper usage. Privacy Laws: EU GDPR: Sweeping requirements for EU citizens/residents. Data Subject Rights (access, rectification, erasure, restriction, notification, portability, objection, automated decision-making). Data Controller/Processor definitions. Privacy by Design/Default. Cybersecurity, Breach Notification, DPIA, DPO. Cross-border data transfers, Binding Corporate Rules, Supervisory Authority, Penalties. US HIPAA: Protects PHI/ePHI (Security Rule, Privacy Rule). US FCRA: Ensures accuracy of consumer credit history, provides data subject rights. Canadian PIPEDA: Ensures consumer data privacy in e-commerce, consent requirements. California CCPA/CPRA: Grants specific privacy rights to California residents (knowledge, disclosure, opt-out of sale, correction, removal, non-discrimination). China CCSL: Data protection, data localization, cybersecurity controls. Brazilian LGPD: Similar to GDPR, establishes National Data Protection Authority. FTC Enforcement: Enforces various US privacy laws (COPPA, CAN-SPAM, GLBA, HITECH, etc.). Privacy Practices: Consent: Data subject's distinct action to grant permission for data collection/processing. Must be recorded. (GDPR = opt-in, CCPA = opt-out). Legal Basis: Organizations must identify the lawful basis for processing (GDPR Article 6.1: contract, legal obligation, vital interests, public interest, legitimate interests). Legitimate Interest: Balancing organizational benefit with data subject rights. Data Governance & Management: Business processes and information system capabilities are central to a privacy program. Cybersecurity Practices: Core part of privacy program; effective cybersecurity is a prerequisite for privacy. Information Systems: Capabilities greatly influence privacy program; privacy drives system capabilities. Reasons for Privacy Governance Avoid regulatory trouble, citizen outrage, and legal action. Oversee transformation to transparent data practices. Ensure data management and protection activities prevent harm to individuals or the organization. Privacy & Security Governance Activities and Results Activities: Risk management, process improvement, event identification, incident response, improved compliance, metrics, resource management, improved IT governance. Results: Increased trust (customers, suppliers, partners), improved reputation (business community). Business Alignment Align with organization's mission, goals, objectives, and strategy. Understand: business model/processes, sources/uses of personal information, culture, asset value, risk tolerance, legal obligations, market conditions, privacy law enforcement. Goals & Objectives: Specific achievements supporting the mission. Risk Appetite: Level of risk an organization is willing to accept (often qualitative: low, medium, high). Monitoring Privacy Responsibilities: Controls, internal audit, metrics, work measurement, performance evaluation, 360 feedback, position benchmarking. Privacy Governance Metrics Purpose: Measure processes, determine strategy effectiveness, understand impact of decisions. Examples: KRIs (risk), KGIs (goals), KPIs (performance). Effective Metrics: SMART (Specific, Measurable, Attainable, Relevant, Timely). Risk Management Metrics: Reduction in incidents, impact, remediation time, new unmitigated risks. (Initial maturity increase may show more incidents due to better detection). Performance Measurement Metrics: Time to detect/remediate incidents, provision/deprovision accounts, respond to requests, discover/remediate vulnerabilities. Convergence Metrics: Gaps/overlaps in asset coverage, data management tools, licenses, skills. Resource Management Metrics: Standardization, privacy/security in procurement, percentage of protected PI records. Developing Metrics in Layers: Tailor metrics for different audiences (operational for IT, business terms for executives). Privacy Strategy Development Definition: "The plan to achieve an objective." Objectives: Strategic alignment, effective risk management, value delivery, resource optimization, performance measurement, assurance process integration. Control Frameworks: Industry standards (ISO/IEC 27701, NIST Privacy Framework, HIPAA, NIST CSF, ISO/IEC 27001, NIST SP 800-53, NIST SP 800-122, CIS CSC, PCI DSS). Risk Objectives: Determine desired risk levels (qualitative or quantitative). Strategy Resources (Inputs): Risk/threat assessments, program charter, vulnerability assessments, maturity assessments, audits, policies, standards, guidelines, processes/procedures, architecture, controls, skills/knowledge, metrics, assets, risk ledger, risk treatment records, insurance, data management practices, critical data, BIA, incident logs, outsourced services, culture, risk appetite. Privacy Program Strategy Development: Categories: Improvements in data management, protective controls, incident visibility/response, risk reduction, cost reduction, increased resiliency. Gap Analysis: Understand missing/augmenting capabilities (processes, technologies, people). SWOT Analysis: Strengths, Weaknesses, Opportunities, Threats. Capability Maturity Models: (CMMi-DEV Levels: Initial, Repeatable, Defined, Managed, Optimizing). Not all processes need Level 5. Road Map Development: Steps to achieve objectives (policy, controls, standards, processes/procedures, roles/responsibilities, training/awareness). Developing a Business Case: Problem statement, current/desired state, success criteria, requirements, approach, plan (costs, timelines). Establishing Communications & Reporting: Board meetings, steering committees, awareness programs, advisories, incident comms, metrics. Obtaining Management Commitment: Essential for funding/resources. Focus on business terms, not fear. Strategy Constraints: Resistance to change, culture, organizational structure, staff capabilities, budget/cost, time, legal/regulatory obligations, acceptable risk. Organizational Inertia: Resistance to change (operational, learning curve, human). Management (34% of Exam) Privacy Roles and Responsibilities Role vs. Responsibility: Role = normal activities (job title); Responsibility = statement of outcomes to support. RACI Charts: Responsible, Accountable, Consulted, Informed. (Variations: PARIS, PACSI). Consider: Skills, Segregation of Duties, Conflict of Interest. Board of Directors: Oversees organization, appoints CEO, fiduciary duty. Requires privacy/security considerations. Executive Management: Carries out board directives, ensures resources. Ratifies/enforces policies, leads by example, ultimate responsibility. Privacy and Security Steering Committees: Risk deliberation, project prioritization, review laws/incidents. Business Process and Business System Owners: Non-technical management accountable for business decisions impacting IT/privacy/security. (Access grants/revocation/reviews, subject inquiries, configuration, function/process definition, physical location). Custodial Responsibilities: IT personnel making access decisions on behalf of system owners. Privacy by Design: Proactively embedding privacy into IT systems and business practices. (GDPR Article 25). Chief Privacy Officer (CPO): Safeguards PI, ensures proper use. Sometimes DPO. Chief Information Security Officer (CISO): Highest ranking info security title. Develops strategies, manages risk program. (Variations: CSO, CIRO, CRO, vCISO). Software Development: Systems Architect: Overall system architecture. Systems Analyst: Application design. Software Engineer/Developer: Application development. Software Tester: Tests changes. Data Management: Data Manager: Data architecture/management. Database Architect: Logical/physical designs. Big Data Architect: Data models for complex sets. Database Administrator (DBA): Builds/maintains databases. Database Analyst: Routine maintenance. Data Scientist: Extracts knowledge from data. Network Management: Network Architect: Designs networks. Network Engineer: Implements/configures devices. Network Administrator: Routine tasks. Telecom Engineer: Works with telecom tech. Systems Management: Systems Architect: Overall system architecture. Systems Engineer: Builds/maintains servers. Storage Engineer: Designs/maintains storage. Systems Administrator: Maintenance/configuration. Operations: Operations Manager: Oversees operations. Operations Analyst: Develops procedures, monitors health. Controls Analyst: Monitors batch jobs. Systems Operator: Monitors systems. Data Entry: Keys data. Media Manager: Tracks backup media. Privacy Operations: Personnel in business departments with PI access (HR, sales, customer support). Security Operations: Designs/builds/monitors security systems. (Security Architect/Engineer/Analyst, Access Administrator). Privacy Audit: Examines process design, verifies policy/control effectiveness. (Privacy Audit Manager/Auditor). Security Audit: Examines process design, verifies control effectiveness. (Security Audit Manager/Auditor). Service Desk: Frontline support. (Service Desk Manager/Analyst, Technical Support Analyst). Quality Assurance (QA): Evaluates IT systems/processes. (QA Manager, QC Manager). Other Roles: Third-party risk management manager, vendor manager, program manager, project manager. General Staff: Understand/comply with policies, proper judgment, reporting. Building a Privacy Operation Scope: Define responsibilities (organization-wide or local). Identifying Privacy Requirements: Culture/values, applicable regulations, legal interpretation, cybersecurity policies. Developing Privacy Policies: Internal: Roles/responsibilities, business processes, protection of PI, consequences for violations, review/audit, measurements, citations. External: Descriptions of collection/protection/uses/transfers, tracking, subject rights, contact info, last update. Developing and Running Data Protection Operations: Built on security controls, operated by IT/security, decisions part of risk management life cycle. Developing and Running Data Monitoring Operations: Data Discovery Scanning: DLP tools scan data stores for specific patterns. Data Movement Monitoring: DLP tooling monitors real-time movement of sensitive data (email, endpoints, file/cloud servers, USB, network ingress/egress). Working with Data Subjects: Inquiries for Data Usage: General or specific requests for PI presence/usage. Requests for Corrections: Updating PI. Requests for Removal: "Right to be forgotten" (must balance with other legal retention requirements). Complaints: Regarding organization's use of PI. Working with Authorities: Completeness of business records is key (process info, DFDs, effective processes, complete records). Need breach procedures for notification. Privacy Training and Awareness Objective: Awareness of proper PI handling, attack types, expected actions, policy compliance. Content: Understandable, relevant, actionable, memorable. Audiences: Corporate Workers, Retail Floor Managers/Cashiers/Workers (tailor content). Information Workers: PI handling. Technical Workers: Security techniques, PI handling. Software Developers: Privacy by design, secure coding (OWASP Top 10). Third Parties: Access to PI. New Hires: ASAP, link access control to training. Annual Training: Refresher, keeps PI/security top-of-mind. Communication Techniques: Email, internal website, video monitors, posters, bulletins. Third-Party Risk Management (TPRM) Definition: Discover and manage risks from external organizations. Cloud Service Providers: Shared responsibility model (define who is responsible for what). Privacy Regulation Requirements: (GDPR: data controller/processor, HIPAA: BAAs, SOX: due diligence). TPRM Life Cycle: Initial Assessment: Evaluate suitability (RFI/RFP, privacy/security sections). Legal Agreement: Negotiate terms (privacy/security program, controls, vulnerability assessments, external audits, incident response/notification, right to audit, periodic review, third-party disclosures, annual due diligence, cyber insurance). Classifying Third Parties: Risk levels (high, medium, low) to tailor assessment rigor. Questionnaires & Artifacts: Request evidence (policies, training, background checks, vulnerability process, insurance, IRP). Tailor length by risk level. Assessing Third Parties: Beyond IT/privacy/security (financial, geopolitical, inherent, breaches, lawsuits). Risk Mitigation: Address unacceptable shortcomings (compel improvements, accept residual risk). Auditing Privacy Operations Purpose: Confirm effectiveness of controls/processes. Privacy Audit Scope: Controls, processes, systems for PI protection/usage. Privacy Audit Objectives: Determine if privacy controls exist and are effective. Types of Privacy Audits: Operational, IS, Integrated, Administrative, Compliance, Forensic, Service Provider. Privacy Audit Planning: Information needed (locations, processes, personnel, tech, policies). Risk-based approach (precede with risk assessment). Statement of Work (for external audits). Establish Audit Procedures (step-by-step instructions). Communication Plan (PBC list, status reports/meetings). Report Preparation (format, content, findings). Wrap-up (deliver report, closing meeting, archive papers). Post-audit Follow-up (monitor remediation progress). Privacy Audit Evidence: Information collected. (Independence, qualifications, objectivity, timing). Gathering Evidence: Interviews, documentation, re-performance, passive observation. Sampling: Statistical, judgmental, attribute, variable, stop-or-go, discovery, stratified. Relying on Other Auditors: External reports (SOC 1/2, ISO 27001) due to specialization/access limits. Reporting Privacy Audit Results: Written report, closing meeting. Auditing Specific Privacy Practices: Privacy Policy: Compliance with regulations/policies, alignment with security. Data Management: Data classification, protection, flows, DLP. Data Collection: Security, policy/regulation alignment, consent, aggregation. Data Subject Requests: Authentication, effectiveness/accuracy/completeness/timeliness of response, recordkeeping, compliance. Data Minimization: Check if more PI is collected than necessary. Anonymization and Pseudonymization: Effectiveness of techniques, re-identification risk. Privacy Incident Management: Investigation policies, computer crime, security/privacy incident response, computer forensics. Audit Standards: ISACA ITAF (Code of Ethics, standards, guidelines, tools/techniques). Privacy Incident Management Definition: Event where PI is inappropriately used/disclosed, or violation of policy. Phases of Incident Response: Planning, detection, initiation, analysis, containment, eradication, recovery, remediation, closure, post-incident review, retention of evidence. Privacy Incident Response Plan Development: Understand processes, policy, data flows, systems. Cooperate with security manager. Identify resources (personnel, forensics, attorney-client privilege, contacts for authorities, prewritten notifications). Incident Response Playbooks: Detailed procedures for specific scenarios. Response Plan Tabletop Testing: Rehearse scenarios. Privacy Continuous Improvement Philosophy: Always room for improvement (accuracy, efficiency, timeliness, risk reduction). Requirement: ISO/IEC 27001:2013 and ISO/IEC 27701. Infrastructure (36% of Exam) Technology Stacks Definition: Set of technologies making up a system (e.g., LAMP, WISA). Hardware: Computers: CPU, main storage (RAM), secondary storage (HDD/SSD), bus, adaptors. Storage: SAN, NAS, cloud-based. RAID for reliability. Networks: Means for computers to communicate. Operating Systems (OSs): Control hardware, facilitate software. Functions: Peripheral access, storage management, process management (isolation), resource allocation, communication, security. Server Clustering: Active-passive, active-active modes, failover. Grid Computing: Distributes tasks across many computers. Virtualization: Multiple OSs on one physical computer (hypervisor, guests). Basis for IaaS. Security considerations: access control, resource allocation, logging, hardening, vulnerability management. Cloud Computing: Dynamically scalable, virtualized resources (IaaS, PaaS, SaaS). Containerization: Multiple apps on single OS, isolated (more efficient than virtualization). File Systems: Logical structure for data storage (directories, files). (FAT, NTFS, EXT3, HFS, APFS, ReFS, ISO/IEC 9660, UDF). Database Management Systems (DBMSs): Stores/retrieves structured info. (DDL, DD/DS, DML). DBMS Structure: Relational (RDBMS - tables, rows, fields, primary/foreign keys, SQL, referential integrity, security, views), NoSQL. Application Servers: Runs business applications. Cloud Services: IaaS (Infrastructure as a Service): Virtualized computing, network, storage. (Elasticity, public/private/hybrid cloud). PaaS (Platform as a Service): Hosted service platform for building/running apps (e.g., Salesforce, Heroku). SaaS (Software as a Service): Vendor-hosted applications (multitenant architecture). Serverless Computing: Customer deploys apps, provider manages OS. MBaaS (Mobile Backend as a Service): Cloud platform for mobile apps (user management, APIs, notifications). Cloud Responsibility Models: Defines who (provider vs. customer) is responsible for what security aspects. Shadow IT/Citizen IT: Departments procuring IT services without IT involvement (CASB, DLP, web filtering help detect). Endpoints Definition: End-user devices (desktop, laptop, tablet, smartphone), connected devices. Laptop and Desktop Computers: Configuration Management: Standard images, central control tools. Security and Privacy: Antimalware, firewall, IPS, DLP, application whitelisting, web content filtering. Users often not local admins. Support: Remote access tools. Virtual Desktop Infrastructure (VDI): Centralized servers run desktops, remote display protocol. (Operational, security, privacy advantages; network connection disadvantage). Mobile Devices: Smartphones, tablets. MDM systems for management. Bring-Your-Own ________ (BYOD/BYOA): Personal devices/apps for work. Risks: data leakage, blind spots. Controls: NAC, application whitelisting, CASB, DLP, UBA. Zero Trust Architecture: New security paradigm. Microperimeters, untrusted endpoints/data centers/networks. Connected Devices and Operational Technology (IoT, ICS, SCADA): Devices communicating on networks. Issues: Poor/no security, lack of updates, outdated OSs, backend data (biometrics, images, location, financial, medical), poor controls for critical infrastructure, increased connectivity. Protective controls: Network segmentation, tight access controls, monitoring. PI collected: Location history, facial recognition, financial/medical data. Remote Access Definition: Remote connectivity to internal network (VPN). Security Controls: Authentication (MFA), Encryption. Client VPN: Software utility installed on endpoint. Clientless (SSL) VPN: Browser-based, no client software (limited to web protocols). Split Tunneling: VPN for internal traffic, direct internet access for external. Risk: Bypasses network controls. System Hardening Definition: Making systems/devices more resistant to attack (configuration settings). Hardening Principles: Single purpose, remove unnecessary subsystems/programs/data/user accounts, limit listeners/connections, change default passwords/identifiers, rename privileged accounts, use up-to-date software. Hardening Standards: Device/system manufacturers, Center for Internet Security Benchmarks, DoD Cyber Exchange STIGs. Security and Privacy by Design: Essential at every layer of infrastructure. Applications and Software (36% of Exam) Privacy and Security by Design Concept: Incorporate privacy/security into systems/applications by default. Seven Foundational Principles: Proactive (not reactive), Preventive (not remedial). Privacy embedded into design (not bolted on). Privacy as the default setting. Full functionality (positive-sum, not zero-sum). End-to-end security (full life-cycle protection). Visibility and transparency (keep it open). Respect for user privacy (user-centric). Systems Development Life Cycle (SDLC) Definition: End-to-end process for developing/maintaining information systems. (S = Systems, not Software). Phases (Waterfall Model): Feasibility Study, Requirements Definition, Design, Development, Testing, Implementation, Post-Implementation. (Iterative/Spiral/DevOps/DevSecOps also used). Feasibility Study: Determine practicality (cost/benefit, business plan, risks). Influencers: Market changes, cost changes, regulation changes, risk changes, business process changes, legal agreement changes, customer requirements/expectations, innovation. Requirements Definition: Describe necessary characteristics. Business Functional: What the system does. Technical: How the system operates (standards, protocols, vendors). Privacy: Protection of PI, prevention of proliferation/misuse. Security: Authentication, authorization, access control, encryption, data validation, audit logging, operational requirements, misuse/abuse requirements. Regulatory: Compliance with applicable laws (location, industry). Disaster Recovery/Business Continuity: Recoverability and continuity. Organizing/Reviewing: Measurable and verifiable. Design: Top-down process, DFDs, ERDs. Gradual complexity. Design reviews by stakeholders. Design freeze. Development: Coding, designing systems, program/system-level documents, user procedures, working with users. Software Acquisition: Customizations, integration, authentication, reports. Source Code Management: Protection, control, version control, recordkeeping. Testing: Verify characteristics. Test Plans: Derived from requirements. Unit Testing: Developers test individual modules. System Testing: End-to-end testing, interface testing, migration testing. Functional Testing: Verify functional requirements. User Acceptance Testing (UAT): Business users approve system. Quality Assurance Testing (QAT): Formal verification of system specs. Implementation: System placed into production. Planning: Physical space, build systems, install software, migrate data. Training: End users, customers, support staff, trainers. Data Migration: Transfer data from old to new. (Record counts, batch totals, checksums). Executing the Cutover: Parallel, geographic, module-by-module, all-at-once. Rollback Planning: Safety net for serious new environment problems. Post-Implementation: Review: System adequacy, privacy/security/audit review, issues, ROI. Software Maintenance: Formal processes for changes (incident/problem/defect/vulnerability/change/configuration management). Software Development Risks: System inadequacy, security/privacy defects, project risk, business inefficiency, regulatory changes, market changes. Alternative Software Development Approaches and Techniques DevOps: Agile development, tighter integration of dev, QA, IT ops. (Data segregation, separation of duties). DevSecOps: DevOps with integrated security design/testing (static/dynamic code scanning). Continuous Integration/Continuous Deployment (CI/CD): Frequent code integration, automated deployments. Agile Development: Iterative, small teams, short sprints. Web-based Application Development: HTML/HTTP, universal client platform (JSON-RPC, SOAP, WSDL). System Development Tools Integrated Development Environment (IDE): Source code editing, version control, compilation, debugging. Computer-Aided Software Engineering (CASE): Automates aspects of development (Upper, Middle, Lower CASE). Acquiring Cloud-based Infrastructure and Applications Options: SaaS, IaaS, PaaS. Considerations: Access control, environment segregation, physical security, regulation, privacy, legal jurisdiction, availability, audit. Applications and Software Hardening Principle: Make applications resistant to misuse/attack. Principles: Input validation (buffer overflow, injection, DoS, data corruption), authentication/session management, temporary files, logging/monitoring, verbose error messages, improper encryption, components with known vulnerabilities, cross-site scripting/request forgery. Testing Applications Code Reviews (manual). Static Code Scans (SAST - automated). Dynamic Code Scans (DAST - automated on running app). Manual Tests (individual forms, fields). Penetration Testing (external party). Bug Bounty (security researchers). APIs and Services Definition: Automated computer interface for dedicated function. Examples: Bulk file transfer, financial processing, call-outs, calculation/banking/payment services. Issues: Application/interface/system security, privacy, data sovereignty. Online Tracking and Behavioral Profiling Purpose: Measure/observe user activity for insights, targeted advertising. Tracking Techniques & Technologies: IP Addresses: Unique numeric value, approximate location. Device Identifiers: IMEI, serial numbers. Web Tracking: Session integrity, usage statistics, advertising. Cookies: Session, persistent, first-party, third-party, super, flash, zombie, HTML5 web storage. Web Beacons: 1x1 pixel images to track views. Location: GPS, browser requests. Device Info: Name, browser, OS, viewport width. Location: Mobile devices, apps use for navigation/business. Eavesdropping: Apps accessing camera, photos, microphone, location, contacts, voice assistant, local/cloud storage, social media, paste buffer. Facial Recognition: Software for login, identification. Privacy concerns. Biometrics: Fingerprint, handprint, iris scan, etc. Contact Tracing: Identifies close proximity to infected individuals (mobile apps). Tracking in the Workplace: Logging activities on devices (web sites, files, email, network comms, location) for security. SSL decryption. Email archiving. Tracking Prevention: Cookie opt-out/blocking/removal, Do Not Track browser setting, privacy mode browsing, Tor browsers, private VPN services, Faraday bags. Data Cycle (30% of Exam) Data Purpose Data Governance: Management's visibility/control over information use. Components: Policies/standards, roles/responsibilities, controls, assessments, reporting. Prerequisite: Organizational change management. Data Inventory: Complete and accurate inventory of all PI. Updates via change management, documented business processes, periodic reviews. Include: File names, contents, last update, access permissions, data owner. Data Classification: Assigning levels of importance/sensitivity. Levels: Registered, Restricted, Confidential, Public. Examples: Personal, sensitive, operational criticality, accuracy/integrity, monetary value. Data Handling Standards: Procedures for handling data at various classification levels. Data Loss Prevention (DLP) Automation: Static DLP: Scan static data stores for specific patterns. Data Tagging: Metadata tagging, watermarking, marking. Dynamic DLP: Detect/intervene in PI transfer (email DLP, USB storage, local/file/cloud server storage, network DLP). Dynamic DLP Actions: Silently note, block, warn/permit with justification. Implementing Dynamic DLP: Run in learn mode first, enlist friendly users, develop response/exception procedures. System and Site Classification: Classify based on highest data classification, operational criticality. Data Quality and Accuracy: Gauge of care for PI fidelity. (GDPR Article 5(1)(d)). Issues: Matches by name/characteristic, data entry errors. Data Flow and Usage Diagrams: Visual schematics (DFDs) to understand how data moves and is used. Data Use Limitation: Collect/use PI only for specified, explicit, legitimate purposes. (GDPR Article 5(1)(b), CCPA Title 1.81.5). Data Use Governance: Internal policies, external privacy policy, controls, monitoring, corrective action, metrics. External Privacy Policy: Describe all primary/secondary uses of PI. Data Analytics: Data Aggregation: Combining databases (e.g., from data brokers) to enrich data. Data Lakes and Big Data: Aggregation of structured/unstructured data for analysis. Machine Learning (ML) and Artificial Intelligence (AI): Improve service/quality, understand customers. Need proper oversight for privacy. Data Persistence Data Minimization: Collect/retain only necessary data elements. PI is an asset and a liability. Collecting Only Required Fields: Rationalize every item. Collecting Only Required Records: Collect only what's needed, remove unneeded. Discarding Data When No Longer Needed: Remove PI when purpose is fulfilled. Minimizing Access: Limit records, personnel, sensitive fields (data masking). Minimizing Storage: Limit where data can be stored (organization-managed systems). Minimizing Availability: Migrate widely accessed data to archival systems. Minimizing Retention: Develop data retention schedules. Challenges: database referential integrity, commingling data, unstructured data, third parties, email. Minimization Through De-identification: Pseudonymization, Anonymization. Data Migration: Transferring data from one system to another. Concerns: Business functionality, information format (ETL), data types, privacy, security, training. Data Storage: Considerations: Data location/sovereignty, data protection, data access, access monitoring. Data Warehousing: Copy of production data for reporting, research, archival. Structured repository. Data Retention and Archiving: Industry Data Retention Laws: Legal requirements for retention periods. Right to Be Forgotten: Data subject requests for removal (must comply unless other laws require retention). Data Archival: Preparing data for long-term storage (online, nearline, offline). Data Destruction: Purposeful act of destroying data so it cannot be recovered. Policy should cover various use cases (laptops, servers, databases, backups, paper). Rigor depends on data sensitivity and risk assessment.